Main Page: Difference between revisions
Telcredstaff (talk | contribs) |
Telcredstaff (talk | contribs) |
||
| Line 16: | Line 16: | ||
=== Cloud-based service === |
=== Cloud-based service === |
||
The combination of IP-connected door controllers and a cloud-based service means that the access control system becomes completely ''independent of location''. It does not matter if you have 10 doors in one location or |
The combination of IP-connected door controllers and a cloud-based service means that the access control system becomes completely ''independent of location''. It does not matter if you have 10 doors in one location or 10 different locations with one door each. Also, you can manage the system from anywhere - inside the same building or from another country. |
||
With a cloud-based service there is ''no need for system maintenance'', i.e. to install upgrades and security patches, do backups, etc. This is all professionally managed by Telcred. |
With a cloud-based service there is ''no need for system maintenance'', i.e. to install upgrades and security patches, do backups, etc. This is all professionally managed by Telcred. |
||
Revision as of 13:01, 20 June 2019
Introduction & benefits
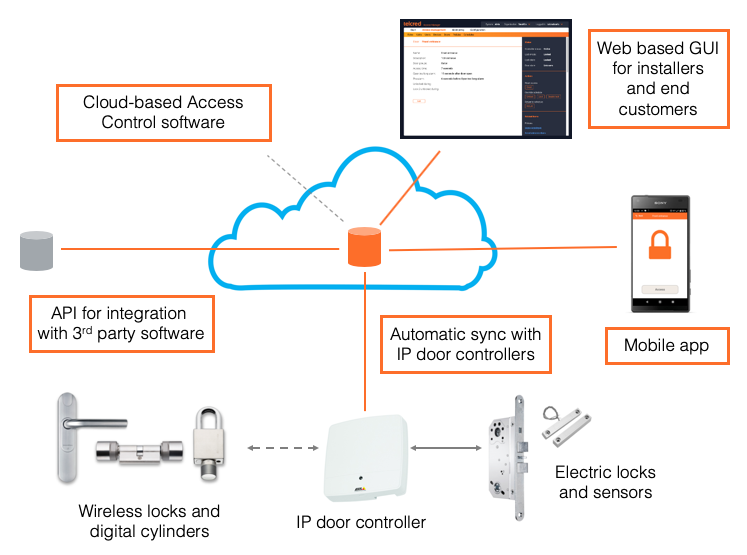
Telcred Access Manager is a software for physical access control, provided as a cloud-service. The solution is designed to work with IP-connected door controllers, specifically the A1001 Network Door Controller, A1601 Network Door Controller, and A9161 Network I/O Relay Module from Axis Communications. The Axis door controllers can also be extended with wireless locks using either SimonsVoss SmartIntego or Assa Aperio.
This online documentation describes the main features of the solution. It is aimed at new customers and partners as a general introduction.
Some of the benefits of Telcred Access Manager include:
- Cloud-based service
- Simple and secure connection of door controllers
- Mobile access with smartphone app or URL
- Simple access for visitors
- Delegated administration
- Strong security
- API for external integrations
Cloud-based service
The combination of IP-connected door controllers and a cloud-based service means that the access control system becomes completely independent of location. It does not matter if you have 10 doors in one location or 10 different locations with one door each. Also, you can manage the system from anywhere - inside the same building or from another country.
With a cloud-based service there is no need for system maintenance, i.e. to install upgrades and security patches, do backups, etc. This is all professionally managed by Telcred.
Even if it is a cloud-based service, the Telcred solution keeps working during temporary network failures. All relevant data is stored locally in the door controllers, which only need to be online to receive updates. In other words, users can still open doors, and no event data is lost, even if the network is down. When the door controller comes back online it will automatically sync pending updates and events with the Telcred service.
Simple and secure connection
Telcred uses the O3C (One-Click-Connection-Component) technology developed by Axis Communications, which makes the door controllers both simple to install and secure. With O3C, door controllers connect to the Telcred service using an encrypted outgoing IP-connection, which means that in most cases there is no need to configure firewalls or routers. After the physical installation, the installer pushes a button on the controller which will then automatically download the connection settings from an Axis server and immediately use them to connect to the Telcred service.
Mobile access
The Telcred Entry app for iOS and Android can be used to open doors as a complement, or alternative, to traditional cards and keyfobs. Opening a door with the app takes less than a second and can be used to let someone in remotely. Alternatively, if all users have the app neither cards nor readers are necessary! Using a smartphone instead of a card has the added benefit of better security. Compared to access cards, most people are less likely to lose or lend their phone to someone else or to share their PIN. Another form of mobile access is through a URL for visitors (see directly below).
Visitor access
A Visit allows the administrator to create a PIN and/or URL that can be used to open one or more doors during a specified time, e.g. in connection with a meeting or an event. The PIN is entered on a reader at the door and the URL can be included in e.g. an email to the visitors. When the visitors arrive, they can let themselves in simply by entering the PIN or clicking the URL in their smartphone email application, without having to receive an access card or install an app. PIN and URL are to be considered low security (anyone who has access to the PIN or the URL can open the door), but for some use cases this is an acceptable tradeoff for the convenience it provides.
Delegation
The Telcred system has been designed to be simple to administrate, yet able to handle large and complex installations. A key aspect of the latter is delegation. With the Telcred solution, it is simple to let different organizations, e.g. tenants or sub-contractors, manage their own doors, users, and access rights. At the same time, simple yet powerful features allow for sharing of users and access rights between organizations. This functionality supports use cases where e.g. a user belonging to one organization must first pass doors belonging to another organization in order to get to the doors belonging to his/her own organization.
Security
The administrator login, often the weakest point in terms of security, can be configured to use two-factor authentication. Another common security weakness is old firmware on the controllers. With Telcred Access Manager it is simple to check and upgrade the firmware remotely. All communication between the door controllers and the Telcred cloud service use strong encryption and the communication between the Telcred Entry app and the cloud service uses strong authentication based on PKI.
API for integration
Telcred provides a modern REST API which can be used for external integrations. The API covers the complete functionality of the system and can be used to extend another security system, e.g. a video management or alarm system, with access control functionality. It can also be used to integrate e.g. a booking system, a member database, or a workforce management system with the Telcred access control service.
System components
Telcred Access Manager consists of five main components:
- Cloud-based server software
- Web-based GUI for installers and end customers
- Smartphone app for iOS and Android
- API for communicating with IP door controllers
- API for integration with 3rd party software
Currently, The Telcred solution works with the A1001 and A1601 Network Door Controllers from Axis Communications. One controller can manage one or two doors with electrical locks, alternatively:
- one door with electrical locks and up to 16 wireless locks from SimonsVoss SmartIntego (via a SmartIntego hub connected to the controller over IP)
- one door with electrical locks and up to 8 wireless locks from Assa Aperio (via an Assa Aperio hub connected to the controller over RS485)
Account structure and delegation
Delegation is a powerful feature in Telcred Access Manager. Below follows a short introduction. More information about delegation can be found here.
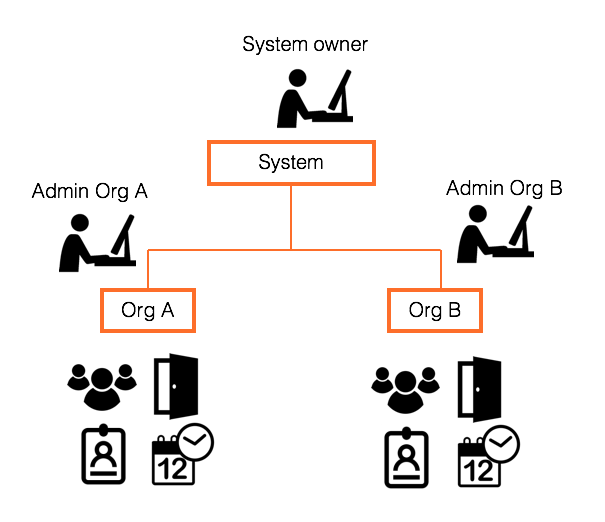
Systems, organizations, officers and capacities
A Telcred customer account is referred to as a system. For any system, an arbitrary amount of organizations can be created. Each organization has its own users, access rights, cards, events, and doors, which can be seen only by the administrator(s) of that organization.
The purpose of having multiple organizations in a system is delegation, i.e. to let administrators with direct knowledge of, and responsibility for, their users users perform the administration without relying on a centralized administration function. A typical example of where delegation can be useful is an office building with multiple tenants. The delegation functionality allows each tenant to manage their own users and access rights without relying on the buliding's owner.
A person doing any type of administration in the Telcred system is known as an officer. These can have different capacities depending on what they should be able to do. The capacities are:
- System owner
- Organization owner
- Administrator
An officer can simultaneously have many capacities and also in many organizations.
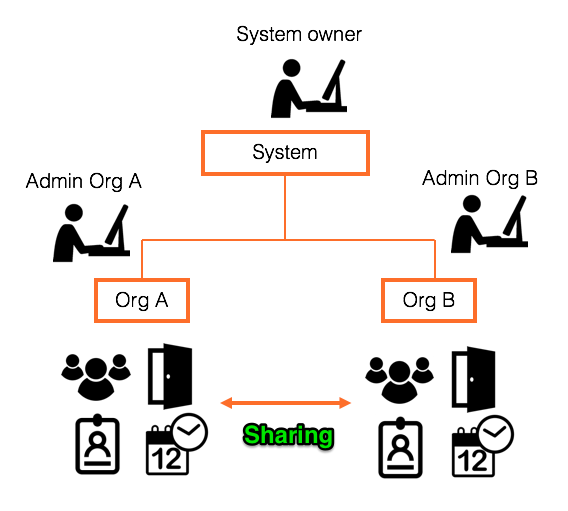
Sharing access rights and users with other organizations
It is possible to share access rights and/or users between organizations (no data is ever shared between systems).
The purpose of sharing access rights is to let an administrator of one organization assign access rights to doors belonging to another organization to his or her own users. One example of this could be where a building owner wants to allow the tenants to manage their own doors, users, and access rights, but also to create access rights to the shared entrance door from the street, which belongs to the building owner.
Sharing users, instead, is useful when a person belonging to one organization often visits premises belonging to another organization. Instead of having to maintain two identities for what is actually the same person, the administrator of the user's home organization can share this user with the other organization, so that that administrator can assign access rights to him or her.
Access control model
Below follows a short overview of the access control model in Telcred Access Manager, i.e. how it is determined which devices, or credentials, that can open which doors, when, and how.
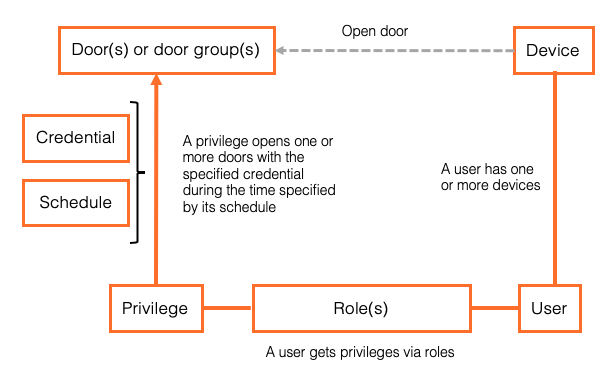
A central concept in Telcred's model is that of a policy. A policy expresses an access right, i.e. the right to open one or more doors. In addition to the door(s) it opens, a policy is defined by the credential that needs to be used (e.g. card + PIN) and an optional schedule that determines when it is valid (the default is always). Schedules can be simple, e.g. Monday to Friday from 08.00 to 18.00, or more complex and exclude e.g. yearly public holidays. Currently the different credentials that can be specified for a policy are:
- card only
- card + PIN
- PIN only
- remote (the Telcred app)
In all cases users receive access rights (i.e. policies) through either a Role or an Assignment. A role can contain many users and many policies, and would typically correspond to the access rights for some group of users, e.g. management, cleaning staff, technicians, etc. Assignments work the same way as roles but have a slightly different purpose. While roles are meant to be few and long lived, assignments are meant to be used to give a user temporary access rights. This way, the need to create temporary access rights does not lead to a large number of roles which could be hard to overview after a while. Both roles and assignments can have a start and end time, during which the assigned policies are valid for the user(s).
A user can own several devices, e.g. a card and a phone, and each will receive the access rights of its owner. If a device is "unlinked" from a user it will lose all its access rights and not be able to open any doors.
Administrator GUI
The administrator GUI is web-based and available at:
The administrator GUI is divided into four main groups:
- Start (latest events and alerts. Offline doors and statistics
- Access management (manage roles, users, cards, doors, privileges, schedules, etc.)
- Monitoring (view events and setup push notifications)
- Configuration (manage door groups and hardware configuration)
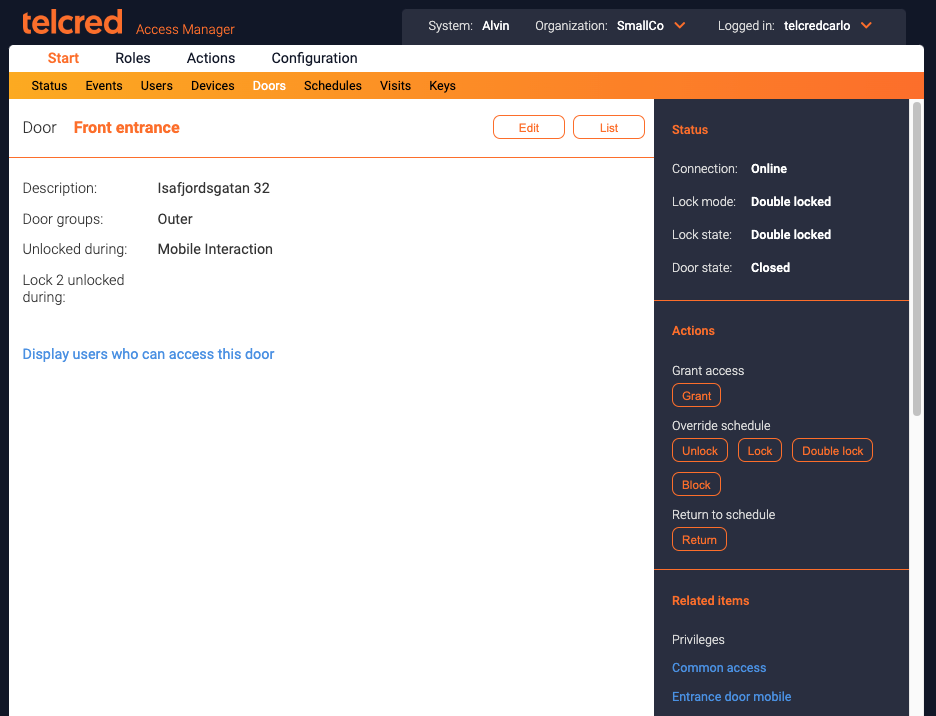
In each group, except the start page, a number of list pages are available from the menu. From the list page it is possible to click an individual item to get to its detail page where it is possible to view or change detailed information.
In the left hand column of the detail page, the item is displayed with its current attributes. In the right hand column there is more information about the current item, such as its current status, available actions, and related items.
Start
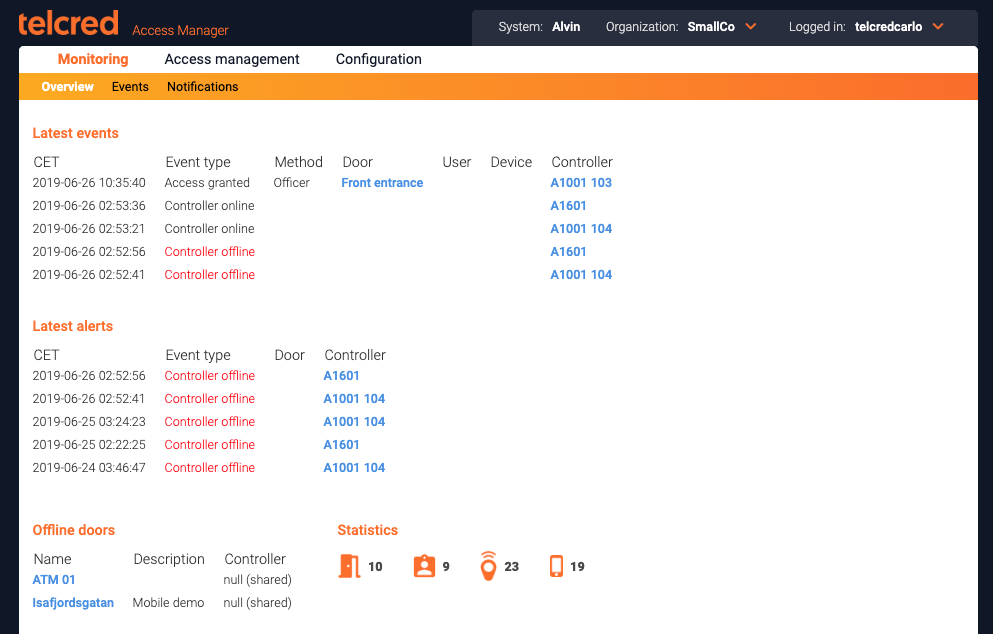
After succesful login, the administrator is presented with a start page showing:
- Latest events
- Latest alerts
- Offline doors
- Statistics on number of doors, users, devices, and mobile devices.
Access management
Roles
Roles is how a user gets access rights to doors. A role connects one or more users to one or more policies. Roles have names and would typically express the user's job function, e.g. "technician" or "student". A user can have many roles.
More information about roles can be found here.
Visits
The purpose of Visits is to enable people who are not registered users in the system to access one or more doors during a limited time. A typical use case could be an event where you want the guests to be able to let themselves in through the front door, but only on the night of the event.
When creating a new visit, the system will generate a URL (web address) that can be pasted into an email and sent to the visitors. When the visitor clicks the URL in the email application on their smartphone it takes them to a web page where they will see an "Open" button for each door included in the visit.
It should be noted that Visits is relatively low security because anybody who has access to the URL can open the door, and it is not possible to know the identity of the actual person who did the opening. On the other hand the access buttons are only visible and possible to use during the time of the visit.
More information about visits can be found here.
Users
Users are the end users of the system that need to be able to open doors. Access rights are always set for a user (using either Roles or Assignments).
A user can be the owner of one or more devices. Every device that a user owns, will inherit the access rights of its owner.
In addition to the mandatory name, a user can have several optional attributes that can be used to sort and filter users, e.g. Department and Employee ID.
A personal PIN can also be set for a user. Some policies require the entry of a correct PIN to open the lock (typically for high security doors or out of office hours). The PIN needs to be numeric and four digits long.
A user can also be shared with other organizations, which is explained in the section on delegation.
More information about users can be found here.
Devices
A device must have a name and a type. Currently, two types of devices are supported: Card with ID and Mobile phone. The latter refers to the Telcred Entry app, which is available for both iOS and Android.
A user can have one or more devices, e.g. a card and a phone or two cards. All devices belonging to the same user will inherit the access rights for that user. A device can only belong to one user at a time, but it is possible to reassign a device to a different user.
More information about devices can be found here.
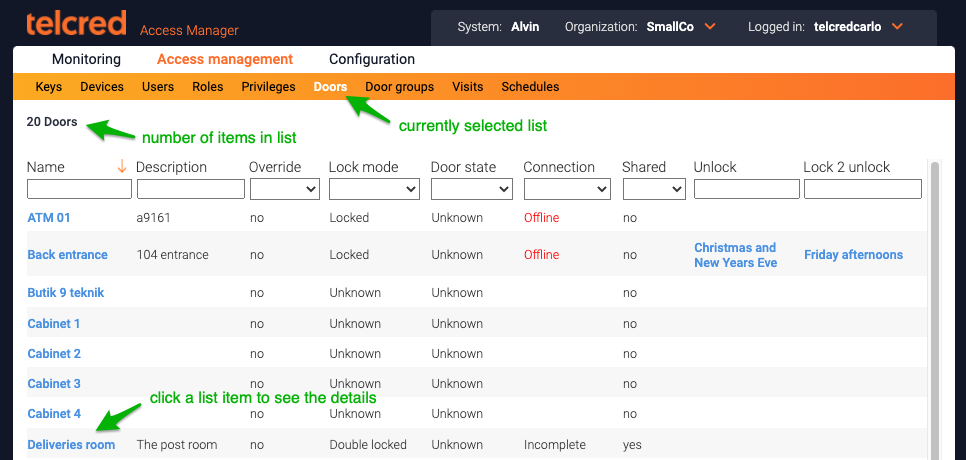
Doors
The Doors tab is used to change the door settings, e.g. access time, "open too long" alarm, and unlock schedule. It is also possible to check the status of the door (if it is locked and closed) and to perform the following actions:
- Grant access
- Manually unlock
- Manually lock
- Return to schedule
More information about doors can be found here.
Policies
Policies express access rights, i.e. the right to open one or more doors. A policy is defined by a combination of:
- one or more doors
- a schedule
- a credential
The supported credential types are:
- card only
- card + PIN
- PIN only
- remote (the Telcred app)
More information about policies can be found here.
Schedules
Schedules are used to:
- Control when a door should be single locked, double locked or unlocked
- Specify when a policy is valid
A schedule contains one or more schedule items. A schedule item can occur once, or recur weekly or yearly.
It is possible to define that a schedule item should be excluded from the normal schedule, which can be useful to manage e.g. public holidays.
More information about schedules can be found here.
Monitoring
Events
Events include the results of user interactions, i.e. access granted or denied, as well as different types of alerts, e.g. door forced open or door left open. In the GUI, events can be filtered and sorted.
Events based on PIN only credentials cannot always be attributed to an individual user. This is because there is no guarantee that the PIN is unique (several users could have the same PIN). If the user's PIN is indeed unique, the system will display the user's name in the event log. If not, no user will be displayed in the event log.
More information about events can be found here.
Notifications
An administrator can setup a Notification in order to get an email, an SMS, or a "webhook" (http request), when certain events occur. It is possible to specify which types of events that should trigger a notification, and when notifications should be generated (e.g. only outside office hours). It is also possible to filter trigger events on e.g. door, user, and method.
More information about notifications can be found here.
Configuration
Door groups
Door groups are collections of doors. The main purpose of door groups is to make it easy to create policies / access rights for groups of doors, without having to list all the individual doors.
Door groups is a generic construct which can be used to express any logical grouping of doors, e.g. site, floor, type of room, security level, geographical area or something else.
More information about door groups can be found here.
Controllers
A controller controls one or more doors and has a number of settings related to the door hardware, e.g. the lock configuration, type of reader, if a door monitor or REX-button (REquest to Exit) is used etc. The controller also has settings related to its own time zone, connection mode and firmware.
Typically, the controller settings will be done by the installer / integrator and not by the end customer administrator.
More information about controllers can be found here.
Hubs
Hubs are only used in connection with wireless locks from SimonsVoss SmartIntego or Assa Aperio. Before a hub can be linked to a controller, it needs to be created here.
More information about hubs can be found here.
Guides & tutorials
Connect an Axis A1001 controller with O3C
To connect an Axis A1001 Network Door Controller to the Telcred service you need:
- The controller
- An Ethernet connection capable of supplying PoE (Power over Ethernet)
- The MAC address of the controller (printed on the device but called S/N)
- The OAK (Owner Authentication Key). This is a code that is printed on a piece paper that is shipped in the box with the controller. If it has been lost, you can get help with retrieving it from either Axis or Telcred
The minimum steps to create the controller are:
- Select Controllers in the main menu and click Add new'
- Give the controller a name
- Make sure the Connection mode is O3C (this is the default)
- Enter the MAC address and OAK
- Click Save
After a few seconds, the status message at the top of the page should now say Waiting for controller to connect. This means that Telcred Access Manager managed to connect to the Axis Dispatch server and claim this controller.
The final step is to push the control button on the controller for 1 - 2 seconds:
This will tell the controller to connect to the Axis Dispatch server and download a certificate with all the information it needs in order to connect to the Telcred service in a secure way, which it will try to do immediately after receiving the certificate.
After the controller manages to connect to Telcred Access Manager its status will be updated to Online.
Detailed information about the A1001 communication settings can be found here.
Set up a new user & provide him or her with access to a door
After a new system has been set up, at least one controller with a reader has been connected, and at least one door configured and connected to the controller, you are ready to start defining and testing the actual access. The steps to do this are (click the links for more details):
- Create a user
- Register a new card and assign it to the user
- Create a schedule
- Create a policy
- Create a role or assignment linking the user to the policy
After these steps, the user should be able to access the door with their card. Note that it can take a few seconds before the access rights have been downloaded to the door controller.
Technical references
API documentation
Virtually everything that can be done through the Telcred GUI can also be done through our APIs. There are three APIs:
- Webhooks API. Used to let another system receive push notifications. The API documentation can be found here.
- Admin API. Used to do everyday admin tasks, such as managing users, credentials, and access rights. The API documentation can be found here.
- Owner API. Used to e.g. manage organizations and officers. The API documentation can be found here.